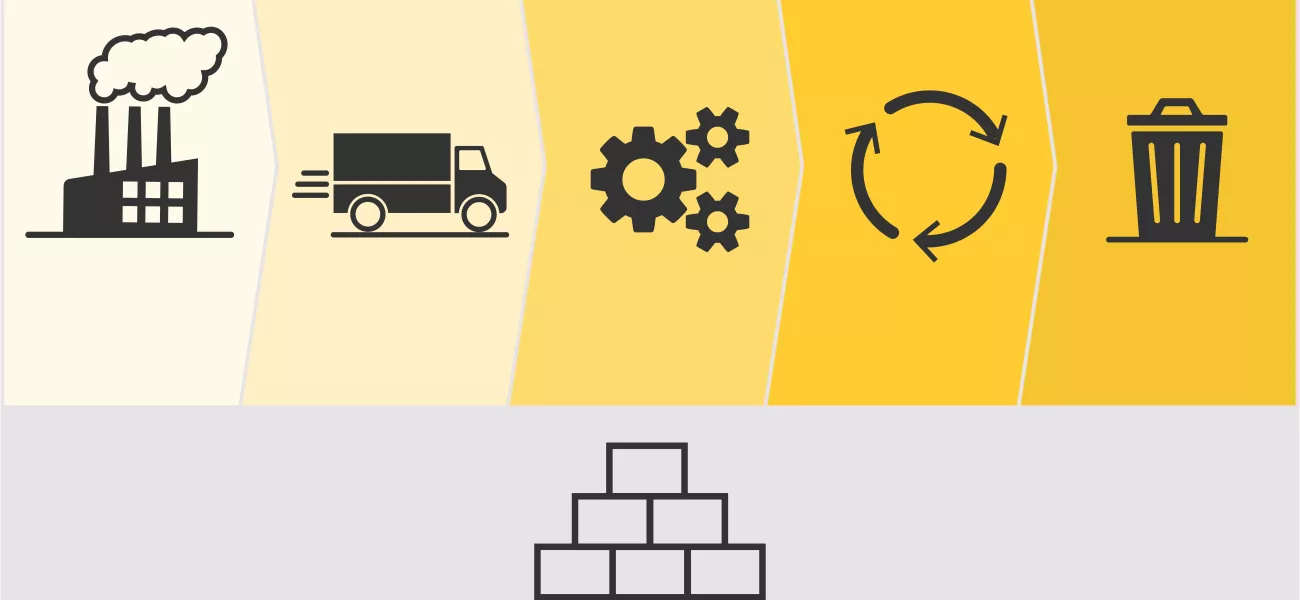
Cybersecurity is high on the agenda of every organization. In an increasingly connected world, any device connected to the network presents a potential cybersecurity risk, and a robust approach to reducing this exposure is essential.
Axis devices, with their built-in cybersecurity controls, are designed to decrease the risk of compromise and enable secure behavior. Our approach is to apply cybersecurity best practices in policies, processes and technologies from development to decommissioning.
In this article, we look at the risks that exist throughout the lifecycle of an Axis device, as well as explore the cybersecurity measures that we take and the support we provide to mitigate those risks.
Secure foundation
For Axis network devices, cybersecurity considerations start at the most fundamental level: the microprocessor and the operating system, AXIS OS. These elements provide the foundation that help secure the products.
The latest version of our system-on-chip (SoC) is ARTPEC-8. An advantage of designing our own SoC is that we have full control over the security features included in the SoC, as well as the processes for deploying those features during production. Such oversight and transparency ensure the hardware and software integrity of the most important component in our devices. When working with third-party SoC vendors, we apply the same security requirements on them as on our own SoCs.
Powerful hardware requires equally powerful software/firmware to make use of our advanced security capabilities. This is where AXIS OS, our Linux-based operating system, comes in. AXIS OS powers a range of Axis devices, giving us unique possibilities to efficiently support cybersecurity measures across a great number of products.
An integral part of software development is ensuring security considerations are taken into account from the start and not as an afterthought. Lack of secure development processes may lead to software releases with easily exploitable vulnerabilities.
At Axis, software development is guided by the Axis Security Development Model (ASDM), which makes security a central focus. ASDM’s defined processes and tools include risk assessments, threat modeling, analysis of code and software composition, and vulnerability scanning. ASDM has the following objectives:
- Make software security an integrated part of Axis software development activities
- Reduce security-related business risks for Axis customers
- Meet increasing awareness of security considerations by our customers and partners
- Create potential for cost reduction through early detection and resolution of vulnerabilities
Production
Lack of supply chain transparency poses a risk that can lead to compromised components in the final product.
At Axis, we strive to keep information, systems, components, equipment, facilities, software, and devices secure throughout our supply chain. Critical components in our devices are procured directly from strategic suppliers and stored in-house. Non-critical components are procured by our manufacturing partners in accordance with our requirements and only from suppliers on our approved vendor list.
We work closely with manufacturing partners to produce the majority of the product lines in our portfolio. We define and monitor production processes, and develop, produce and provide critical production equipment as well as the system for testing components, modules and products at the different stages during production. All software and tests are developed in-house. Production data from our manufacturing partners is shared 24/7 with us, enabling real-time data analysis. The high level of transparency makes it possible for us to assess potential security risks in collaboration with the manufacturing partner, as well as implementing mitigation plans.
During production, a key cybersecurity element that is installed on an Axis device is Edge Vault, a secure cryptographic compute module that protects keys and sensitive data from being accessed and tampered with in the event of a security breach. Among the keys that are encrypted and securely stored on Edge Vault is the Axis device ID. An Axis device ID is unique and involves a collection of certificates, including a digitally signed version of the globally unique serial number of the Axis device. The device ID guarantees that the device is a genuine Axis product.
Axis also ensures the authenticity of a device’s firmware by installing a signed AXIS OS. The digital signature guarantees that the firmware is indeed from Axis and hasn’t been compromised. AXIS OS also ensures that any new firmware to be downloaded and installed on a device is an Axis signed firmware. As a second line of defense, Axis secure boot checks for the signature of the firmware at every boot.
Before Axis devices are shipped to distributors, and subsequently, system integrators, they pass through one of the Axis Configuration and Logistics Centers where they are subject to further quality control.
At every site within the Axis supply chain, from the component supplier to the distribution center, we have high requirements on access controls to ensure the physical security of the facilities.
Distribution
A possible risk during shipment is the manipulation of a device’s firmware or its configuration. Measures involving signed firmware and secure boot – in combination with making a factory default on the device – offer protection from malicious modifications.
Implementation
Risks during implementation can come from putting compromised or inadequately hardened products on the network. They may result in unauthorized access to the network, extraction of sensitive data or assets such as private keys and certificates for use in malicious attacks, or they may enable altered data to be transferred between network endpoints. So how does Axis help you to address these issues?
At initial implementation, Axis recommends performing a factory default on the device. This action guarantees that the device is completely free of unwanted software or configuration since the only software remaining is AXIS OS and its default settings. In the process of starting up, secure boot on the device checks if the device’s firmware is signed by Axis. Secure boot occurs every time the device starts or powers up. If it detects that it is not an Axis signed firmware, the device will not run it, preventing any unauthorized operation from occurring. Secure boot provides a defense against any firmware that may have been altered after leaving the Axis Configuration and Logistics Centers or while in operation.
To be sure that only genuine Axis devices are implemented on your network, you can verify the Axis device ID using IEEE 802.1x authentication or when establishing a secure network connection through the HTTPS protocol. Edge Vault on an Axis device supports the processing of all cryptographic operations requiring private keys and enables secure device authentication using the IEEE 802.1AR standard.
The AXIS OS Hardening Guide provides best practices and technical advice for anyone involved in implementing Axis devices. It establishes a baseline configuration to address common threats and takes a layered approach to security.
A tool for efficiently configuring and managing Axis devices locally is AXIS Device Manager. The device manager enables batch processing of important installation and security tasks, such as managing device credentials, deploying certificates, disabling unused services, and upgrading AXIS OS.
In service
While in service, a device can be exposed to threats from deliberate attacks or unintentional mistakes. Risks can arise from running firmware with known vulnerabilities that an adversary can exploit, updating devices with unauthenticated firmware, or letting secure configurations lapse.
Axis works continuously to identify and limit risks associated with discovered security vulnerabilities in our offerings. We address them by providing security patches in AXIS OS and making public notifications.
To maintain the cybersecurity of an Axis device, ongoing support and making frequent AXIS OS updates are essential. Axis provides two ways of keeping AXIS OS up to date: the active track and the long-term support (LTS) track. In the active track, AXIS OS is continually updated with new features and security patches. In the LTS track, only security patches are included in AXIS OS updates. AXIS OS updates are provided free of charge and all information about an update can be found on the AXIS OS Portal.
When upgrading firmware, the device’s existing signed AXIS OS will automatically check that the new firmware to be downloaded is also a signed firmware. If not, the new firmware cannot be installed. This ensures that only authorized firmware is loaded onto a device, and rebooting the device with secure boot provides an additional layer of control that the firmware is indeed an Axis signed firmware.
For efficient maintenance while devices are in service, we offer AXIS Device Manager Extend as a complement to AXIS Device Manager. AXIS Device Manager Extend provides an intuitive dashboard that allows you to manage Axis devices remotely. It simplifies scaling of crucial maintenance tasks, such as upgrading AXIS OS, defining, applying and enforcing security policies, and managing applications.
As an approved Common Vulnerability and Exposures (CVE) Numbering Authority (CNA), Axis follows industry best practices in managing and responding – with transparency – to discovered vulnerabilities. Axis uses the commonly known CVSS rating system (Common Vulnerability Scoring System) to rate vulnerabilities related to either Axis-developed code or third-party open-source code. Axis assesses vulnerabilities in open-source code according to how relevant they are for our products when best practice recommendations are applied. You can subscribe to the Axis Security Notification Service to receive information about vulnerabilities and other security-related matters for Axis products. More details are available in the Axis Vulnerability Management Policy document.
In addition to supporting you in maintaining your Axis device, we also provide signed video. Signed video provides added trust and assurance that the video has not been tampered with after it left the camera. Signed video adds a cryptographic checksum into each video frame, which is then signed in Edge Vault by a unique key that is attested by the Axis device ID. This makes it possible to prove the video origin without having to prove the whole chain of trust. And with the help of an Axis file player, signed video also makes it possible to see if an exported copy of the video has been altered or parts removed from the original recording. Proving video authenticity is particularly important in an investigation or prosecution.
Decommissioning
Having devices on the network that are no longer supported and have known, unpatched vulnerabilities is a risk to the system. Leaving sensitive data available on devices after disposal also presents a risk. So what measures can help address these issues?
Beyond acting as a tool to manage and secure devices within the surveillance solution, AXIS Device Manager Extend allows you to track the status of warranties for all devices in the system, including product discontinuation and end of support information.
Should you need to return a device to Axis or one of our partners – either for repair, replacement, or decommissioning – we offer guidance regarding the removal of data and device sanitation as part of the return merchandise authorization (RMA) process.
When decommissioning an Axis device, a factory default should be made to erase all configurations and data.
Mitigating risks
Staying cybersecure is about managing risks. It’s about understanding the risks, taking active decisions to manage those risks, and ensuring best practices are implemented for your own system. As a vendor, we take our responsibility by following best practices. We also support you with guidance, technologies, tools and services to help you mitigate risks when using our products.